Are Passwords a Thing of the Future? Or a Thing of the Past?
Passwords have been used for a very long time. Nowadays we use them in our digital world as a form of authentication. But why do we use them? Are passwords strong enough as authentication mechanism? Are there ways to make this mechanism stronger? Or are there other mechanisms that will replace passwords?These are just some of the questions that arise when considering the future of passwords and their usage. As technology continues to evolve, it is important to stay informed and aware of the latest developments in online security to protect our personal information and online identities.
Posted on Thursday May 4th, 2023 at 0:00
Why do we use passwords?
You might wonder why do we actually have to use passwords. That’s a good question: why can’t we just use our emails address to access our accounts?
Passwords are used as a mechanism to authenticate yourself. This way you can prove to the website that you are who you claim to be. If we would not use passwords (or any other form of authentication), anyone else that knows your email address would be able to say ‘Hello, I am person x and I want to access this account’ and the website will let her/him in. Of course we don’t want this to happen. This is why passwords-based authentication is so commonly used. It was the first authentication mechanism.
Strength of passwords
Using strong passwords is essential. They are like the Jedi of the digital world, wielding the power to protect our online identities from the dark forces of the internet (a little hint to the publication date of this article 😉 ). A strong password will protect you from the brute Force attacks. Unfortunately the use of passwords alone is not enough to secure your accounts nowadays. Even if you use strong/complex passwords. Attackers can easily steal your credentials through phishing attacks or by installing a keylogger. That’s why the use of passwords alone is not enough.
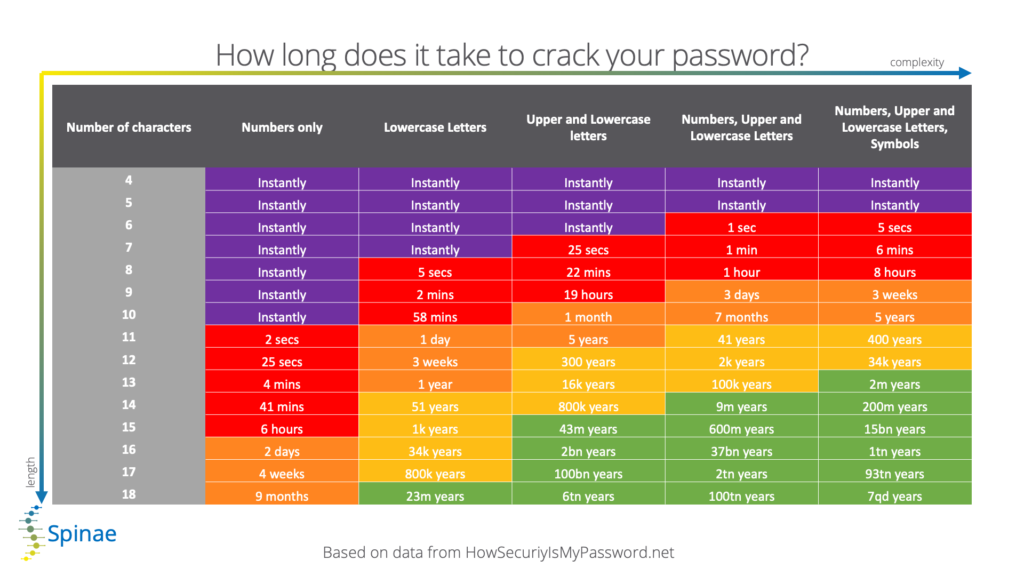
The below chart shows how long (short?) it takes a cyber criminal to crack your password with respect to length and complexity. This influences the allowed lifetime of your password: if it can be cracked in e.g. 1 month (10 characters, lower and upper case) then that password must be changed more than once per month.
Optimizing the authentication mechanism
The first step of optimizing this authentication mechanism is by using strong passwords. A good password manager can help you with this. It allows you to store all your credentials in a secure place.
Another step to secure this mechanism is by enabling multi-factor authentication on all your accounts. By enabling this, an attacker that was able to retrieve your password wont be able to login to your account because they won’t have the second factor.
Other mechanisms that could replace passwords
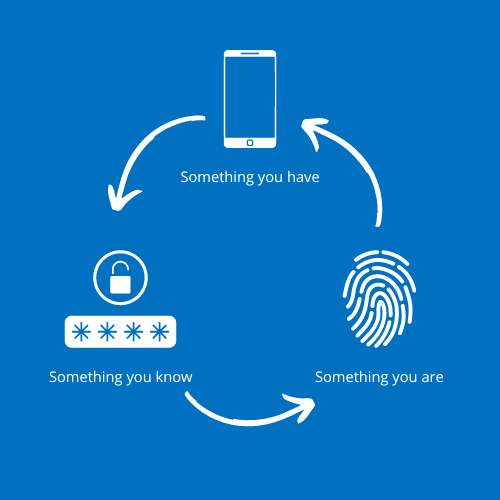
There are three factors of authentication that are commonly used nowadays.
Something you know:
This on is used the most: logging in to websites with a username and password.
Something you have:
The ‘something you have’ factor refers to a physical object where you have access to. This can be a key, a security badge or even your phone. With this form of authentication, the user still has the responsibility of keeping this object secured. As we know, giving this responsibility to the users is not always a good idea. They may lose the physical object, it can be stolen or cloned.
Something you are:
This factor of authentication is focusing on bio-metrical data. Think about face recognition or fingerprints as form of authentication. Although this might seems like the best option, only focusing on this is not ideal either. What would happen if we show a picture of someone to a face-recognition authentication factor? Will it allows us to log in? And what about twins, will they be able to hack each others accounts?
The future of passwords
By now we all know that the use of passwords is not ideal and that they are not very user friendly. Luckily, a passwordless form of authentication is coming up. The FIDO Alliance is an open industry association that started in 2013. Their mission is to improve authentication mechanisms. The FIDO Alliance developed a standard for passwordless authentication.This authentication mechanism is called Passkeys. A passkey replaces the use of passwords and it has a 2FA mechanism built in. The use of passkeys is very easy. When creating an account using a passkey, the website will ask you to confirm that you want to create a passkey and then stores it in your (Google, iCloud or Microsoft) account. Before storing them, the website will ask you to confirm your identity. This will be done using bio-metrical data like a fingerprint or face-recognition. The next time you want to login, you select the passkey option, select the passkey that you have created and identify yourself by scanning your face or finger.
Conclusion
All three authentication factors have there advantages and disadvantages. Thats why we recommend to use a combination of 2 of these factors. This is also known as Multi-Factor Authentication (MFA). For example: something you have and something you are: a YubiKey with a fingerprint reader is a good example of this. But you don’t have to limit yourself to 2 factors. You can also use all three of them. For example log in to a website with a username and password (something you know), then use your phone (something you have) to open your Authenticator app. By adding you Authenticator app to a secure folder, you can add an extra layer of authentication (bio-metrical for example). This way you can implement all three factors of authentication to secure your accounts. As mentioned previously, this is good example of MFA. Something you know (your credentials), something you have (your phone) and something you are (your fingerprint of face-recognition).
Passwordless authentication is growing and might lead to the disappearance of passwords. Because it has MFA build in, it is a more secure mechanism. Attacks like phishing will become less effective since you wont use passwords. However, it also has disadvantages. Because we will store our passkeys in our Google, iCloud, Microsoft or other identity provider account. This is a lot of responsibility you give to these vendors which you have to be aware of, as this introduces other risks.
Would you like to discuss your current way of authentication? Talk about the future? Get in touch with our experts : we are happy to help you!

