Inside Penetration Testing
Part I: Tools, Methods & Approach
In this first chapter of a three-part series we will delve into the mind of a professional application pentester. This series will primarily focus on the methodology of a pentester and will provide an insight into their thoughts on the concept.
So when it comes to pentesting, where does an ethical hacker start? What’s their approach? How do they navigate through the unknown?
Gathering Information
Each application is unique so there is no set way to perform a pentest. However the starting approach remains the same – gathering information. It’s one of the most important steps for getting a good understanding of how exactly the application works. Knowledge is power and knowing enough about the application is essential to perform a pentest more effectively.
If for instance you’ve found out that the application has been written in .NET, which is a framework for building applications, then there will be no need in trying to inject a PHP code into the application to try and gain unauthorized access.
Technologies & Functionality
When continuing to gather information, you must identify the technologies used. Fortunately, a pentester has a range of tools at his disposal. A tool that’s recommended is Wappalyzer. A strong aspect of this tool is its ability to quickly and accurately detect and analyze the technologies used.
After identifying what technologies are used, a pentester must try to gain more information about the functionality of the application. For this, there are two different methods used.
1. Fuzzing
This method is all about trying to identify API endpoints and (hidden) webpages. The process revolves around trying a lot of different URL’s and seeing if they give a valid response or not. In some cases this could already lead to finding critical vulnerabilities. If there’s a .git folder or config file found in the list, then there could be database credentials found.
2. Web Proxy
In this method a pentester starts looking at the requests made. When applying this method, a preferred tool among the ethical hackers is Burp Suite.
This tool captures every request made when browsing through a site. This comes in very handy when trying to get information about all the functionalities of a site. By using each feature once, Burp Suite will provide a list of all the endpoints. It will even allow you to repeat these requests with other values.
So when an attacker has a full overview of the application, he starts to investigate functionalities more in depth. This is done because there are always some features or functionalities that look a bit off.
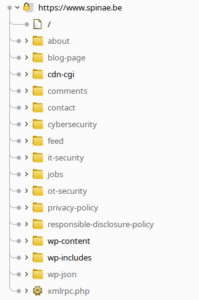
(a full overview of an application)
Final Thoughts
In conclusion, our first exploration into the mind of a pentester has provided us with a first quick glance at their methodology and preferred tools and techniques. Like in each digital work field, a pentester must continuously hone his skills to stay ahead of challenges. Mostly having the right tools and approach will help him navigate the cybersecurity landscape.
Spinae Security Specialists Are Here to Help
Relying on the right technology, also applies for companies you cooperate with. At Spinae, we aim to earn your trust by giving you accurate and realistic cybersecurity advice. With our approach and perseverance we want to showcase how committed we are in keeping your company secure. Find out more about application pentesting here: IT Security Penetration Tests – Spinae
If you’d like to learn more about cybersecurity or how we can assist your company, feel free to reach out to us: https://spinae.be/contact
About the author
Timo De Clercq is our lead application pentester at Spinae. As a teenager he started developing his own applications and immediately found out that things could be used in other ways than intended when not being careful. He got his degree as Cyber Security Professional at Howest University College Brugge, Belgium and started his professional career as security researcher at Howest University College. He later came on board at Spinae as our lead application pentester. In his free time, he is a bounty hunter on several cyber security bounty hunting platforms.


